Windows Security
25 posts
• Page 2 of 3 • 1, 2, 3
Re: Windows Security
Well, let's all keep an eye on this.
- Clifton
- Site Admin
- Posts: 732
- Joined: Tue Jan 14, 2014 1:04 am
Re: Windows Security
Here's an update on this. I still occasionally see js files being flagged as the aforementioned trojan. It's typically some but not all of the target platforms for a particular page. Only when the files are compressed do they get flagged. I've been able to work around the problem by authoring a small change to the page in question. This is usually enough to allow republishing without incident.
I have not seen this recently with any of my global lesson files, but back when it was happening I found that any change to the book could remedy the problem. Also, I have never seen this behavior with any of the powerpac files.
I can find no pattern of when this can occur. I have many pages that are quite similar, yet only one of them might trigger the problem. My current project happens to use a lot of rich text, so maybe there is some magic sequence of text that compresses into a file that attracts attention.
So in summary, I'm working around it for now in the hope that MS will eventually get more selective and not have so many false positives! ~Andy
I have not seen this recently with any of my global lesson files, but back when it was happening I found that any change to the book could remedy the problem. Also, I have never seen this behavior with any of the powerpac files.
I can find no pattern of when this can occur. I have many pages that are quite similar, yet only one of them might trigger the problem. My current project happens to use a lot of rich text, so maybe there is some magic sequence of text that compresses into a file that attracts attention.
So in summary, I'm working around it for now in the hope that MS will eventually get more selective and not have so many false positives! ~Andy
- Andy
- Posts: 47
- Joined: Tue Sep 09, 2014 3:40 pm
Re: Windows Security
Hi Clifton and Andy,
I was just about to write a post on another subject and saw this conversation. I can't add much but I thought I should emphasize that it's not just Powerpac files that trigger a response from Windows Security in my case. Apart from one js file all the others have been small exe files created with AutoIt. Following Clifton's advice to add product details to all exes I discovered the current method of doing this with AutoIt files here: https://www.autoitscript.com/autoit3/docs/keywords/pragma.htm Since updating my files with this new 'pragma' system I have not seen any Windows security interventions but that may or may not be significant. I too have wondered whether different rules are applied by Microsoft in different countries. Being rather cynical I suspect they think they can get away with dubious practices more easily in countries where IT expertise is somewhat under par.
But this is not a big deal for me. I just add certain folders to the security exclusions and this solves the problem. The program that I hope to finish sooner or later is designed to run on a web server where Microsoft can't get at it.
John
I was just about to write a post on another subject and saw this conversation. I can't add much but I thought I should emphasize that it's not just Powerpac files that trigger a response from Windows Security in my case. Apart from one js file all the others have been small exe files created with AutoIt. Following Clifton's advice to add product details to all exes I discovered the current method of doing this with AutoIt files here: https://www.autoitscript.com/autoit3/docs/keywords/pragma.htm Since updating my files with this new 'pragma' system I have not seen any Windows security interventions but that may or may not be significant. I too have wondered whether different rules are applied by Microsoft in different countries. Being rather cynical I suspect they think they can get away with dubious practices more easily in countries where IT expertise is somewhat under par.
But this is not a big deal for me. I just add certain folders to the security exclusions and this solves the problem. The program that I hope to finish sooner or later is designed to run on a web server where Microsoft can't get at it.
John
- John Robin Dove
- Posts: 486
- Joined: Thu Jan 23, 2014 4:35 am
Re: Windows Security
Hi John,
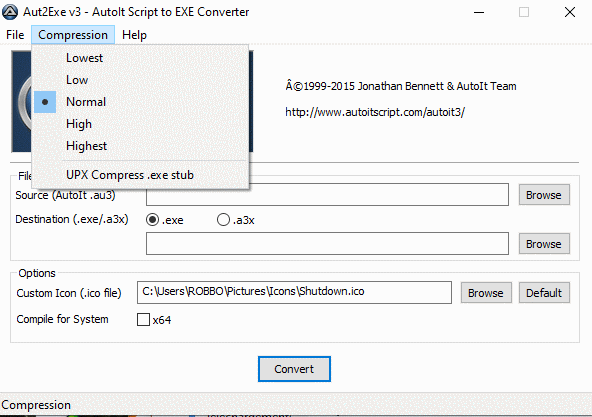
If you are using AutoIt, make sure to turn OFF UPX compression of your exe's. Several sources have suggested that this will help prevent false positives.
Clifton
If you are using AutoIt, make sure to turn OFF UPX compression of your exe's. Several sources have suggested that this will help prevent false positives.
Clifton
- Clifton
- Site Admin
- Posts: 732
- Joined: Tue Jan 14, 2014 1:04 am
Re: Windows Security
Thanks, I'll check it out.
- John Robin Dove
- Posts: 486
- Joined: Thu Jan 23, 2014 4:35 am
Re: Windows Security
Not that it is a big deal, but I guess turning OFF UPX compression also improves performance of your scripts by changing how memory is allocated each time the script is run. This probably also helps keep anti-virus software a little bit at bay.
- Clifton
- Site Admin
- Posts: 732
- Joined: Tue Jan 14, 2014 1:04 am
Re: Windows Security
I've just had a look at AutoIt2.exe and as far as I can see UPX has never been activated.
Not trying to rush you but did you see my other post entitled 'Right mousedown'?

Not trying to rush you but did you see my other post entitled 'Right mousedown'?
- John Robin Dove
- Posts: 486
- Joined: Thu Jan 23, 2014 4:35 am
Re: Windows Security
The compiler you are using is the default one that comes with AutoIt3.
However, if you use the AutoItSciTE Editor, you will benefit from a number of nice features when compiling exe's.
Just an FYI.
However, if you use the AutoItSciTE Editor, you will benefit from a number of nice features when compiling exe's.
Just an FYI.
- Clifton
- Site Admin
- Posts: 732
- Joined: Tue Jan 14, 2014 1:04 am
Re: Windows Security
Hi Clifton,
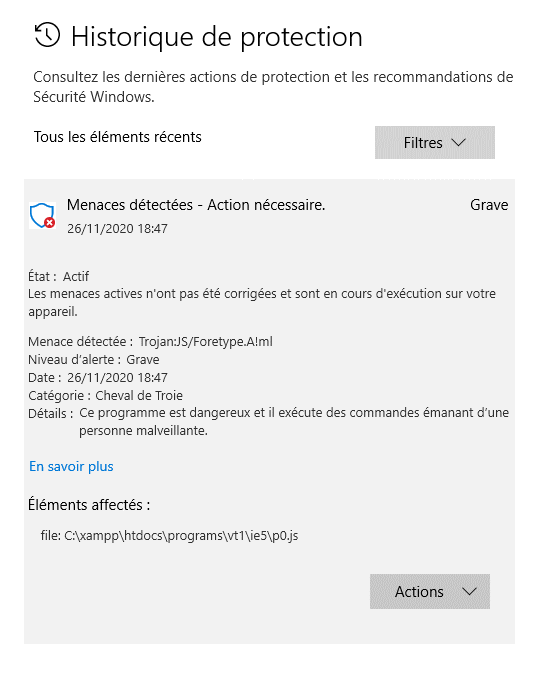
A different js file has been targeted this time.
John
A different js file has been targeted this time.

John
- John Robin Dove
- Posts: 486
- Joined: Thu Jan 23, 2014 4:35 am
Re: Windows Security
p0.js is auto-generated by ToolBook during export. Obviously these are false positives.
For what it's worth, try changing the path to NOT include the word "programs" as this may trigger suspicion from MS Defender.
At any rate, once your application is running from the web, you will not have to deal with these Defender flags.
For what it's worth, try changing the path to NOT include the word "programs" as this may trigger suspicion from MS Defender.
At any rate, once your application is running from the web, you will not have to deal with these Defender flags.
- Clifton
- Site Admin
- Posts: 732
- Joined: Tue Jan 14, 2014 1:04 am
25 posts
• Page 2 of 3 • 1, 2, 3
Who is online
Users browsing this forum: No registered users and 2 guests
