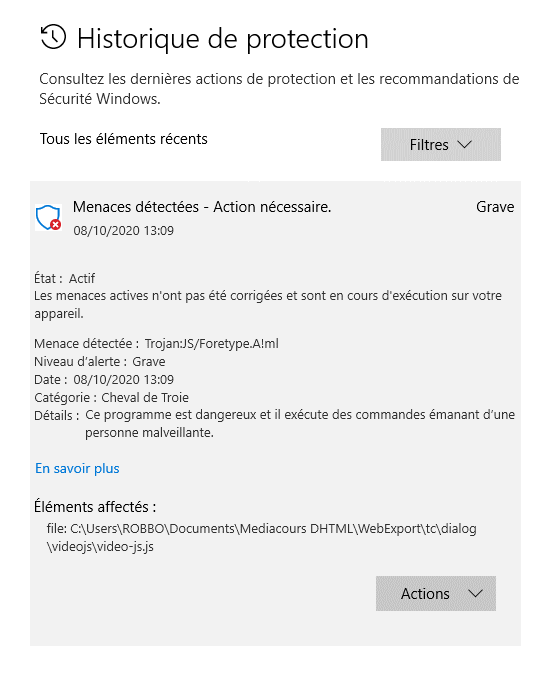
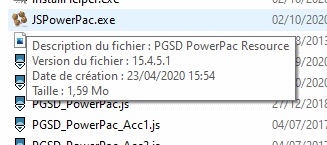
Can you provide the path to the js files that are being flagged?
For example:The PowerPac installation includes js files but they never get flagged. But if your flagged files are in your users/documents folder, then the secuity software may trigger an issue because generally such files are not assumed to exist in that location. I have ToolBook/PowerPac exports all over my system, but most all of these are in drives other than drive C where development files are kept.
I've also not had anyone indicate that files are being flagged or quarantined which are part of an installed application that contains js files. That application gets installed into the "Program Files (x86)" folder.
As a test, I let Windows Defender scan an external drive which contains hundreds of js files. Windows Defendee did not flag a single one. NONE were considered malicious. This leads me to think it is not so much the js files as it is the location of them on your system that makes Windows Defender hiccup. It this test case, there was a mix of LZW compressed js files and uncompressed ones.
As another test, I let Windows Defender scan the installation folder for the PowerPac (C:/Program Files (x86)/PGSD ToolBook Plugins/). Again, NO THREATS were detected. Both this and the prevous test were performed with normal Windows Defender settings.
I must admit, I then copied several ToolBook/PowerPac exports to the users/documents folder and then ran a scan. However, on my system the scan still says NO THREATS found.
It would be good to actually find the test scenario that triggers js files as being flagged as a threat. Any help you can provide certainly appreciated. If the real problem is with 3rd party anti-virus, then anything is possible as the scan results from such programs may be "all over the page."